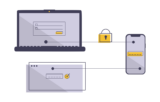
Fingerprint and facial recognition now provide convenient access for users to mobile devices and computers, and increase security, too.
Tech Notes
What’s your tolerance for risk?
The first step in increasing organizational security is to establish a baseline understanding of your organization’s workflow and existing policies. Think about and document how your organization would manage a cybersecurity event under current circumstances: How long would your downtime be? How would that impact your ability to serve your clients? What would be the real cost of recovery?
JumpCloud’s “Partner Success” interview with Michael Horst
Macktez COO Michael Horst talks to Chris Tate from JumpCloud about how our years-long partnership with JumpCloud has grown as JumpCloud’s features, our clients’ needs, and workforce trends have evolved.
Contact form failures revealed by DMARC
DMARC reports reveal what’s missing. Without DMARC, some emails can fail authentication and soon start getting rejected.
Turn on multi-factor authentication right now
As work-from-anywhere becomes the norm, access to confidential information is no longer protected by physical access to an office or to a MFA is one of the most effective and easiest layers to add for preventing this kind of unauthorized access and improving your digital security.
Insurers play catch-up on cybersecurity policies
When you next try to renew your cybersecurity insurance, you might find the process for approval and the policies available are quite different from before.
Microsoft finally honors DMARC
Configured properly, and then monitored and adjusted over time, DMARC can reduce cybersecurity risks and increase deliverability for legitimate email. (Configured improperly, however, DMARC instructions could result in all of your outgoing email getting rejected — so you need to know what is going on under the hood.)
Las Vegas ransomware incident highlights need for cybervigilance
A ransomware incident ensnaring two of Las Vegas’s largest casinos made national headlines last month and inspired a lot of questions about ransomware, multi-factor authentication, single-sign on, access management, and vishing. What happened? What went wrong?